base3200 - One more message sent by R3cursiv3 Hacker was intercepted.
You challenge is to decode the message and reveal the flag.
The recovered message is on the attached zip file.
Solved by 89 Teams Created by @ea_sh
Solution
I received a zip file w/ a giant(45mb) msg.txt
..let's inspect header/footer:
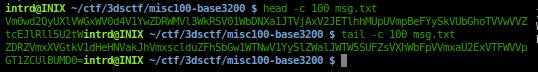
loooks a true base64..
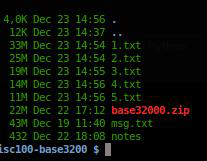
yes, after some cat msg.txt | base64 --decode >> n.txt, look at the file size reducing, it is enconded w/ a recursive base64, and the title gives the tip
Title=base3200.. 3200/64=50 <- it means, encoded w/ base64 50 times.
Wrote a py to decode 50 times
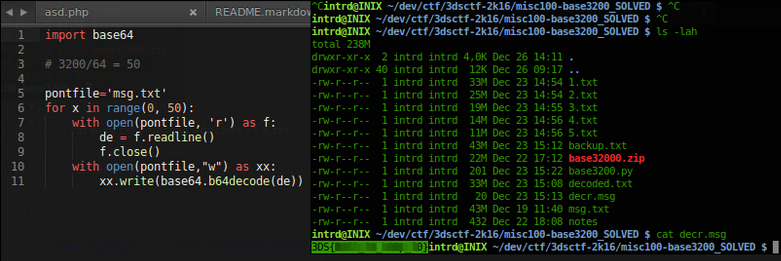
Flag: 3DS{CENSORED}
 intrd has spoken
intrd has spoken